Many of us have periodically seen news stories involving the unknowing exposure of a company’s sensitive information through publicly accessible cloud storage areas due to the lack of proper access controls. The issue can often be traced back to an understanding of the proper security controls needed to protect sensitive information, which can be convoluted. Most notably discovered are open Amazon Web Services (AWS) Simple Storage Service areas, otherwise known as S3 buckets. So, exactly how do you find an open cloud storage area? Let’s walk through a process.
Amazon S3 Bucket Search
Amazon S3 is one of the original offerings that was designed for AWS. “Buckets” are accessible over Representational State Transfer (or REST) Application Programming Interface (API) web services. Amazon S3 is inherently designed to use unique names, which means that anyone on the AWS cloud can register any easily remembered name that is globally unique to AWS. A common Domain Name System (DNS) naming convention is used to identify S3 buckets. Amazon names have endings such as s3-website-us-east-1.amazonaws.com and s3.amazonaws.com. With the known domain names, unsecured S3 buckets on the Internet are identified and indexed by search engines. Therefore, the first place you should consider looking for open S3 buckets is a search engine such as Google or Bing. Using a few Google search directives (also known as “dorks”), the following example (site:s3-website-us-east-1.amazonaws.com filetype:pdf) provides a search for S3 buckets containing Adobe document files.
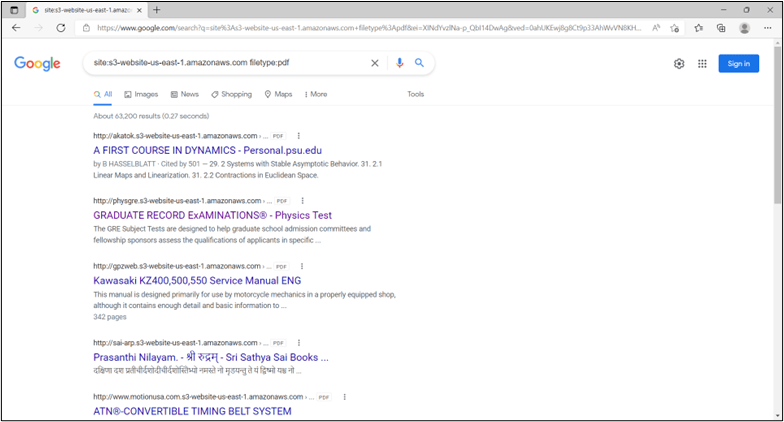
Example: Google Search Results for S3 Bucket Files
Gobuster S3 Bucket Search
A common security tool that can be used to search for unauthenticated S3 buckets is Gobuster. The freely available tool is found on the GitHub code repository. This tool can be used by providing a list of potential S3 bucket names and a pattern file. The format would be similar to: gobuster s3 -w <bucketlist> -p <pattern file> -v. To ensure success, be certain that the list is in all lowercase letters. Please keep in mind that if you do receive results from the search, it isn’t necessarily indicative that the underlying files can be accessed and modified. This is simply a representative index of the S3 bucket as viewable from the Internet. However, you may be able to access a variety of files through your searches such as web site support files including logs, image, and video galleries.
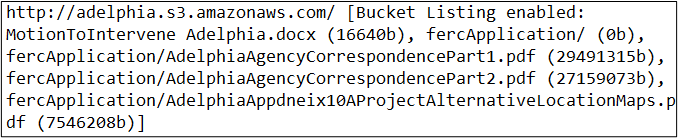
Example: Result from Gobuster S3 Bucket Search Using List of US Cities as Input
Azure Cloud Storage Areas
Now that we have described ways to uncover Amazon S3 buckets, Microsoft Azure cloud storage areas can be located in a similar fashion. Researchers from CyberArk recently found terabytes of data publicly exposed in Azure.
The Azure cloud storage equivalent to the Amazon S3 bucket is the Binary Large Object, or Blob. However, there are some expanded types of storage environments in Azure. In addition to the Blob, these include tables, queues, and file storage. While, like AWS, storage can be accessed with REST API services, it can also be accessed with Server Message Block (SMB). Azure Active Directory Domain Services (AD DS) is required for SMB file server access. This type of access can be permitted from the Internet.
Azure Open Storage Search
To assist in your quest for unexpected data disclosure, a common DNS naming convention is used to identify Azure storage areas which, similar to AWS, is globally unique in Azure. Names have endings such as files.core.windows.net. Therefore, once again, you can leverage a search engine to locate information on open Azure storage.
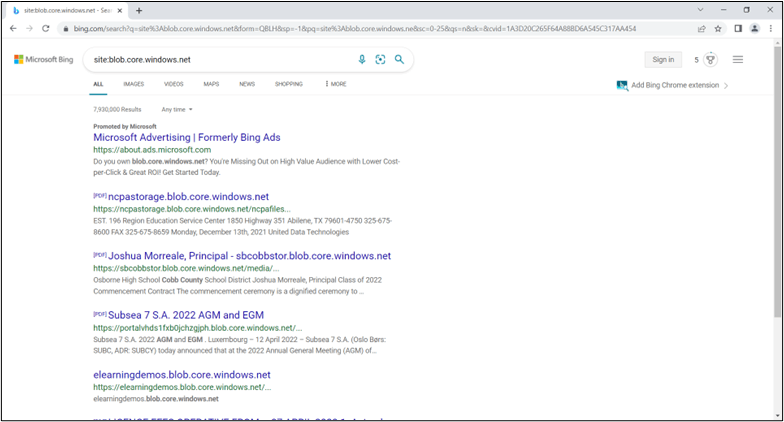
Bing Search Results for Azure Storage Account Sites
Basic Blob Finder
A freely available tool located on GitHub to find unauthenticated Azure Blobs is Basic Blob Finder. Basic Blob Finder is similar to the Gobuster tool previously mentioned. Again, you simply supply a list of potential storage area names along with their container names. The format would be similar to: basicblobfinder.py <storage area/container>.
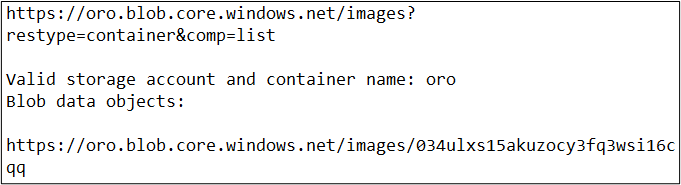
Example: Result from Basic Blob Finder Azure Storage Area Search
Grayhatwarfare
Now that we have endured the effort of using Google, Bing, and some other free tools to locate open storage areas in both AWS and Azure, it turns out that somebody else might have already done a lot of the hard work for you and you’re just reinventing the wheel. However, knowing the basic approaches to searching for open storage provides a great deal of value in the event that crowdsource-type websites are unavailable or disappear.
A group named Grayhatwarfare has a collection website for current (and historical) open storage areas for AWS and Azure. In addition to site filtering, the capability exists to search for file extensions which can result in the discovery of sensitive information such as credentials in configuration files.
It should now be evident that finding sensitive information on open cloud storage areas can be as easy as running a search on a website.
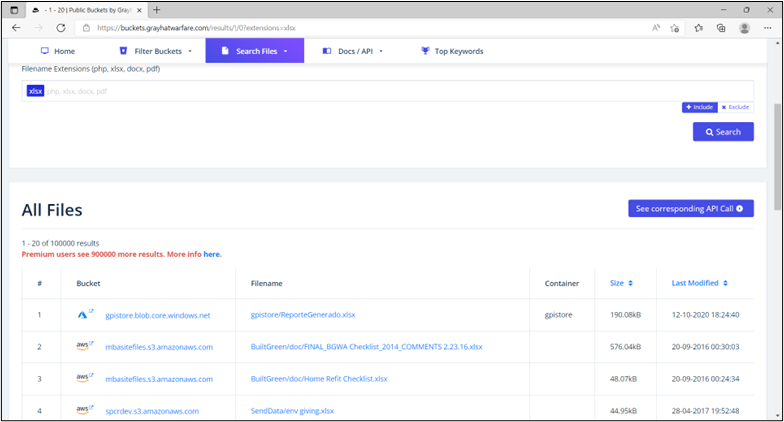
Example: AWS and Azure Results from Searching for File Extension .xlsx on buckets.grayhatwarfare.com
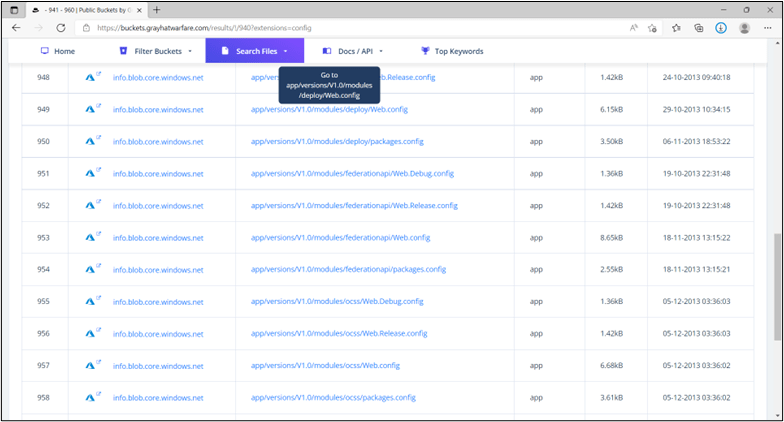
Example: Azure Results from Searching for File Extension .config on buckets.grayhatwarfare.com
Cloud based storage has become a staple in today’s digital environment. However, the ease with which this technology can be used comes with a great deal of danger. To compound difficulties, it can be very difficult to implement security controls to prevent the accidental public sharing of sensitive information. Therefore, organizations must proactively search for unknown risks. Combining focused searches for Amazon S3 buckets and Microsoft Blobs, along with Dark Web Searches, can provide a level of confidence to counteract the unknown risks of sensitive data that is publicly available.
LBMC is here to help and answer any questions you might have. Contact our team today!
