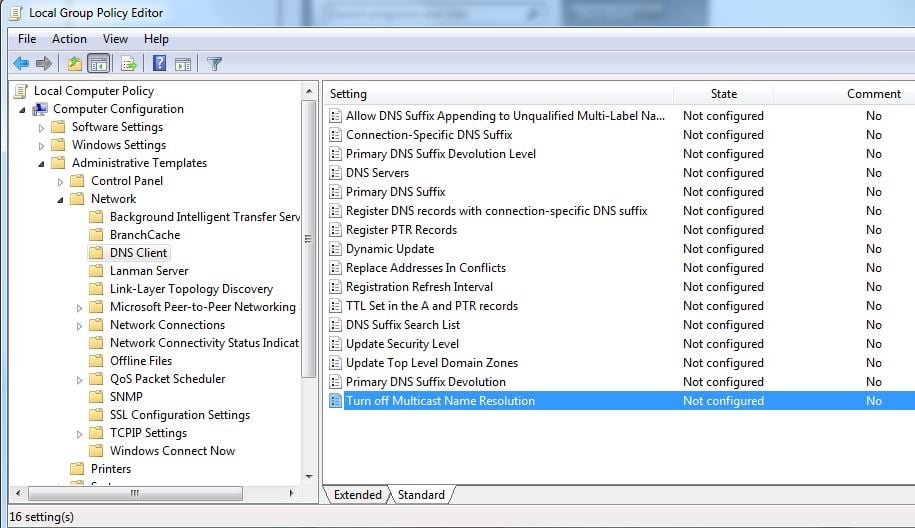
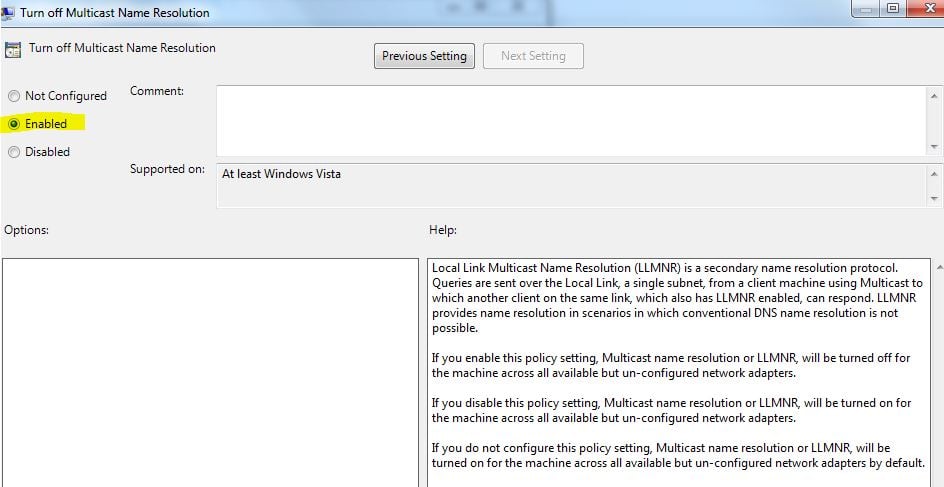
The problem is all computers on the same local network receive these broadcast requests, and if they so choose can respond to the request without any checks that the system responding is legitimate. Here’s how the hack works:
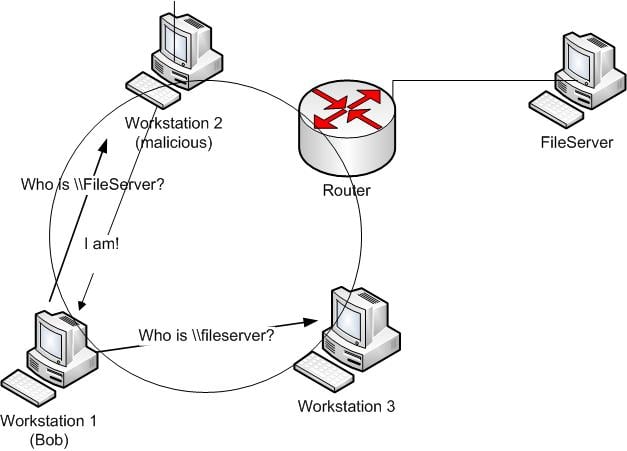
When a workstation makes a broadcast request looking for a resource (in our example \fileserver) a malicious computer (Workstation 2 in our example) can respond, tricking the requesting computer (Workstation 1) that they are the resource they are looking for. In a corporate environment (domain joined computers), the requesting computer will automatically attempt to authenticate to the malicious computer over normal Microsoft networking ports (TCP 445). The malicious computer runs spoofing software to capture the authentication process and will obtain the User ID and challenge/response password hash of the user logged-in to the requesting computer (Bob on Workstation 1 in our example). With the password hash (Bob’s) the hacker can now use offline password cracking tools such as Hashcat or John the Ripper to crack the password. Note: a Challenge/Response password hash cannot be used in a “pass-the-hash” attack only a raw LanMan or NTLM hash can be passed. However, most passwords can be cracked in minutes using modern word mangling rules built into Hashcat or John the Ripper. Or the malicious computer can relay the credentials from the requesting computer to a 3rd system and authenticate as that user – without knowing the password! This is called an SMB Relay attack. There are many tools to carry out this attack, SpiderLabs has a great standalone tool called Responder and Metasploit has auxiliary modules for this attack as well.
On a typical corporate network, an attacker can obtain the challenge/response password hashes of many users within minutes.
Once a hacker (or pen tester) has a valid user ID and password they can quickly use the access of that user to find other issues and obtain access to sensitive data. The beauty of this attack (from the hacker’s perspective) is that it is very stealthy. No port scanning or other noisy network traffic that might set off alerts.