Cybersecurity Maturity Model Certification (CMMC)

The Cybersecurity Maturity Model Certification (CMMC) accreditation framework impacts the U.S. Department of Defense (DoD) contractors, supply chain, solution providers, and systems integrators.
What is the Cybersecurity Maturity Model Certification (CMMC)?
CMMC is the Cybersecurity Maturity Model Certification, which is in development to help protect the Department of Defense’s supply chain from cybersecurity related threats. The DoD is including the requirement for certification against the CMMC maturity model in future contracts, which includes subcontractors as well. The supply chain, referred to in DoD circles as the Defense Industrial Base or DIB, could potentially be the target of the nation’s adversaries because vendors in the DIB may have sensitive or confidential information related to the nation’s security. The idea is that without a secure foundation, all functions are at risk. Cybersecurity should serve as the foundation across all aspects of the nation’s defense industrial base.
Why was CMMC created?
Global cyber-attacks on the US Department of Defense (DoD) supply chain from foreign adversaries, industry competitors, and international criminals are at the forefront of US national security concerns. Countries like China, Russia, and North Korea exfiltrate over $600 billion in the US (1% global GDP), according to Ellen Lord, Undersecretary of Defense for Acquisition and Sustainment. Even today, these bad actors are using the COVID-19 pandemic as cover for their nefarious actions while organizations are distracted as they extend their business operations from physical offices to individuals’ homes.
Who does CMMC apply to?
Three hundred thousand companies are involved in the Defense Industrial Base (DIB) to some extent, whether they are contracting directly with the DoD or are subcontractors to larger firms. Regardless of the relationship to the DoD, all supply chain contractors will need to achieve at least Level 1 certification.
What is the CMMC Certification Process?
The CMMC initiative is largely being driven by the DoD Office of the Under Secretary of Defense for Acquisition. Generally, the certification process will flow similarly to a lot of other certifications or cybersecurity assessments, such as ISO or FedRAMP. First, an accreditation body was put together in order to form the rules and framework around the entire assessment and certification process. Assessment bodies must then apply to the accreditation body to accredit their organization to be able to perform CMMC assessments and then train and certify their workforce to perform the assessment work. Once an assessment body completes the accreditation, training, and personnel certification process, then they will be able to perform CMMC assessments to certify clients.
Who are CMMC Assessors?
The process has been moving forward throughout 2020, beginning with the formation of the CMMC accreditation board, or CMMC-AB. The AB was initially compromised of a board made entirely of volunteers working to put together a framework for assessment bodies, professionals, and organizations seeking certification. The framework includes the standards themselves, the requirements for accreditation, the process for assessment and certification, and training. The CMMC-AB established a beta program of provisional assessors. These assessors are a select smaller pool from the assessment space that is currently being trained to perform assessments on a provisional basis. The DoD has selected very specific contracts that are currently going through the acquisition process with the new CMMC requirements to serve as a beta test for the beta/provisional assessments. This carefully thought out test step will allow compliance assessors, the accreditation body, industry, and the DoD CMMC PMO to perform a few assessments and then evaluate the process to determine what is going to work best.
After these provisional assessments occur, the CMMC-AB will move forward with larger-scale training availability, assessor firm accreditation, and finalization of requirements. CMMC-AB is still very early in the process of establishing the certification ecosystem. The current phase of the pilot is considered the Provisional phase and involves a limited number of provisional assessors and their associated certification bodies (or third-party assessment organizations). The DoD is piloting no more than 15 contracts this year and will not fully implement the requirement until 2025.
In February 2021, Provincia Government Solutions (PGS), a leader in NIST and FISMA assessments and strategic partner of LBMC, became one of the first organizations recognized as a CMMC-AB approved Certified Third-Party Assessment Organization (C3PAO). Read more about how PGS and LBMC are partnering to provide CMMC assessment services: https://www.24-7pressrelease.com/press-release/479289/provincia-government-solutions-among-first-organizations-to-achieve-c3pao-status-and-announces-cmmc-partnership-with-lbmc
When is CMMC going to be required?
Generally, CMMC is something you may need to worry about if you are a contractor or vendor to the DoD, or subcontractor to a DoD contractor. However, the DoD and CMMC accreditation body have indicated that the DoD will be deploying the requirement in new contracts over a period of years. The CMMC requirement is not expected to be inserted into active contracts. Even though you may not have to worry about it right this minute – it’s never too early to start considering your security posture.
Have questions about CMMC? LBMC can help your organization prepare for and obtain CMMC accreditation. Contact us now.
Podcast: What is the Cybersecurity Maturity Model Certification (CMMC)?
In this episode of Cybersecurity Sense, Caryn Woolley joins Bill Dean to discuss the Cybersecurity Maturity Model Certification (CMMC). Tune in to learn why the Department of Defense (DoD) created the new cybersecurity assessment to improve the security of government contractors and subcontractors. In this episode, Caryn explains the five certification levels that reflect the maturity and reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information on contractors’ information systems. She also provides more information on the current state of the CMMC and what steps DoD contractors can take now to prepare.
CMMC Framework
According to the Office of the Under Secretary of Defense for Acquisition & Sustainment, the CMMC framework contains five maturity processes and 171 cybersecurity best practices progressing across five maturity levels. The CMMC maturity processes institutionalize cybersecurity activities to ensure they are consistent, repeatable, and of high-quality. The CMMC framework is coupled with a certification program to verify the implementation of processes and practices.
What are the CMMC 5 levels?
The CMMC practices provide a range of mitigation across the levels, starting with basic safeguarding at level 1, moving to the broad protection of Controlled Unclassified Information (CUI) at level 3, and culminating with reducing the risk from Advanced Persistent Threats (APTs) at levels 4 and 5.
What are some practical examples of how CMMC takes you through the 5 levels of cybersecurity?
From the standpoint of a common security process,
Example 1 – Incident Response:
- Level 1, Basic Cyber Hygiene, does not address incident response directly
- Level 2, Intermediate Cyber Hygiene, document the incident response procedures
- Level 3, Good Cyber Hygiene, the manage phase, includes practices to manage reported incidents and report to appropriate levels
- Level 4, Proactive Cyber Hygiene, includes continually reviewing for incidents and establishing the capability to respond
- Level 5, Advanced / Progressive Cyber Hygiene, incident response capability includes anomalous activity and establishment of a CIRT
The requirements:
| Level | Number | Practice |
| 2 | IR.2.096 | Develop and implement responses to declared incidents according to pre-defined procedures. |
| 3 | IR.3.098 | Track, document, and report incidents to designated officials and/or authorities both internal and external to the organization. |
| 4 | IR.4.101 | Establish and maintain a security operations center capability that facilitates a 24/7 response capability. |
| 5 | IR.5.102 | Use a combination of manual and automated, real-time responses to anomalous activities that match incident patterns. |
| 5 | IR.5.108 | Establish and maintain a cyber incident response team that can investigate an issue physically or virtually at any location within 24 hours. |
Example 2 – Perform configuration and change management:
- This capability is not required for level 1 maturity.
- At level 2, controls focus on documentation of control practices and we introduce the security configuration, change control tracking, and security impact analysis
- level 3, controls around configuration become more mature and progress to the managed state, requiring physical and logical access restrictions, removal of non-essential functions, and whitelist/blacklist access software restrictions.
- Level 4 introduces application whitelisting based upon management review
- Level 5 introduces a process to continually review effectiveness, which introduces optimization. Viewing in this fashion show the increasing maturity, the improved security posture, and how the capability around configuration becomes more and more ingrained in how the organization does business.
The requirements:
| Level | Number | Practice |
| 2 | CM.2.064 | Establish and enforce security configuration settings for information technology products employed in organizational systems. |
| 2 | CM.2.065 | Track, review, approve, or disapprove, and log changes to organizational systems. |
| 2 | CM.2.066 | Analyze the security impact of changes prior to implementation. |
| 3 | CM.3.067 | Define, document, approve, and enforce physical and logical access restrictions associated with changes to organizational systems. |
| 3 | CM.3.068 | Restrict, disable, or prevent the use of nonessential programs, functions, ports, protocols, and services. |
| 3 | CM.3.069 | Apply deny-by-exception (blacklisting) policy to prevent the use of unauthorized software or deny-all, permit-by-exception (whitelisting) policy to allow the execution of authorized software. |
| 4 | CM.4.073 | Employ application whitelisting and an application vetting process for systems identified by the organization. |
| 5 | CM.5.074 | Verify the integrity and correctness of security critical or essential software as defined by the organization (e.g., roots of trust, formal verification, or cryptographic signatures). |
Additions by Security Domain Across the First 3 Levels
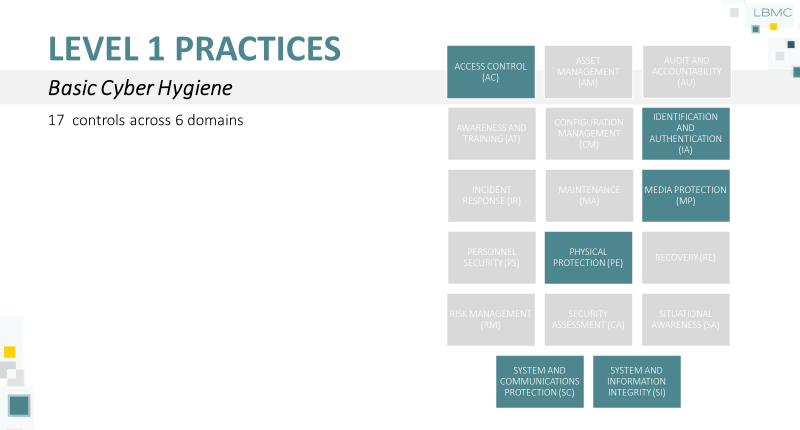
- Level 1, 17 controls across 6 domains:
- ACCESS CONTROL (AC)
- IDENTIFICATION AND AUTHENTICATION (IA)
- MEDIA PROTECTION (MP)
- PHYSICAL PROTECTION (PE)
- SYSTEM AND COMMUNICATIONS PROTECTION (SC)
- SYSTEM AND INFORMATION INTEGRITY (SI)
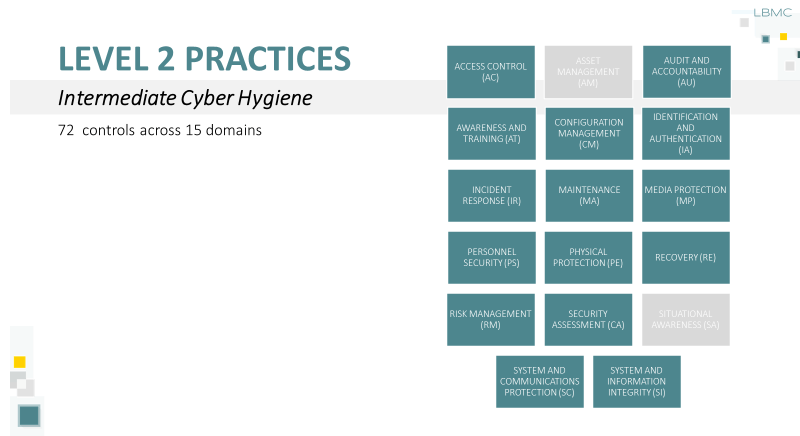
- Level 2, 72 controls across 15 domains, which adds:
- AUDIT AND ACCOUNTABILITY (AU)
- AWARENESS AND TRAINING (AT)
- CONFIGURATION MANAGEMENT (CM)
- INCIDENT RESPONSE (IR)
- MAINTENANCE (MA)
- PERSONNEL SECURITY (PS)
- RECOVERY (RE)
- RISK MANAGEMENT (RM)
- SECURITY ASSESSMENT (CA)
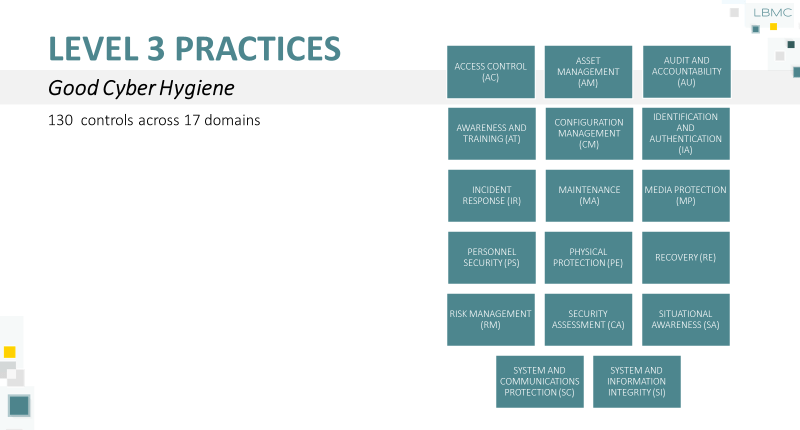
- Level 3, 130 controls across 17 domains, which adds:
- ASSET MANAGEMENT (AM)
- SITUATIONAL AWARENESS (SA)
The majority of companies will fall into Level 1, so what are those 17 controls?
The 17 controls really are the things that most companies are already doing, you just might need to formalize them a bit to be ready for an audit. Those basic include using user IDs and effective passwords, limiting system access, and functions, sanitizing media, limiting/logging/controlling physical access and control over visitors, controlling the system boundary (usually through firewalls and a DMZ), patching vulnerabilities, and, last but not least, malicious code protection that updates and scans.
Here is what the 17 controls look like:
- Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Verify and control/limit connections to and use of external information systems.
- Control information posted or processed on publicly accessible information systems.
- Identify information system users, processes acting on behalf of users, or devices.
- Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems.
- Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- Escort visitors and monitor visitor activity.
- Maintain audit logs of physical access.
- Control and manage physical access devices.
- Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- Identify, report, and correct information and information system flaws in a timely manner.
- Provide protection from malicious code at appropriate locations within organizational information systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
What does it look like when I move on to Level 2?
There are 55 additional controls, bringing us to a total of 72. That list is, perhaps, a bit too long to include them all here. But to give you an idea of what we are looking at.
- Access control and Identification / Authorization, which at level 1, focused on limiting access to systems and functions, use of authentication mechanisms and identifiers, and maintaining control over access to external and publicly access systems, now goes further. Level 2 adds privacy/security notices, limitations on portable device storage, least privilege, session locks, logon attempt limits, wireless control, remote access control, and specific password management and encryption requirements
- System and Communication, which at level 1 requires firewall type protection at the boundary and implementation of a DMZ, adds controls around remote control of collaborative tools and encryption of network device management sessions.
Also, why would a company go for a level 2 certification, when DoD is only requiring a level 1 or a level 3? Level 2 is meant to show a transition state for a company that is working toward level 3. If for instance, your organization wished to pursue a contract requiring a level 3 cert, but your security posture is not quite at that point yet, you could achieve level 2 certification to better showcase your current transitionary state. Currently, the contracted certification level is not required until contract reward. So, the transition state of level 2 certification could help your organization show progress at contract proposals ahead of contract award.
Ok, tell me about Levels 3, 4, and 5?
Level 3 is another major step up, with an additional 58 controls for a total of 130 controls. The lift to get to level 3 can be significant for a less mature security program. Level 3 is good cyber hygiene. While most companies will be addressing the majority of the risks presented at level 3, they might not be doing it at the specificity of these requirements. In addition, having the ability to show implementation of these controls could be a challenge. At level 3, you not only have the policy / procedure requirements, but also the plan associated with ongoing implementation of controls.
To go back 2 of the previous examples, access control, which goes from 4 at level 1 to 14 at level 2, now adds 8 more for a total of 22 controls. And then identification and authentication, goes from 2 at level 1 to 7 at level 2, now adds 4 more for a total of 11 controls. The types of controls that are added for these 2 domains – additional controls for wireless, remote access, segregation of duties, privileged users, mobile devices, encryption, and multifactor authentication.
System and Communication – starting from 2 at level 1 to 4 at level 2, now adds 15 more for a total of 19 controls. Additional requirements include more specific firewall, remote access, and encryption techniques, new requirements around mobile code, VOIP, sessions controls, and key management.
Level 4 and Level 5 introduce the least of proactive cyber controls and advanced cyber protection. These levels are intended for companies with information that has more sensitivity than those at level 3. During that initial pilot phases of CMMC, the focus is on Levels 1 to 3 with level 4 and 5 being considered a future state. Nonetheless, there are proposed controls for the levels.
Let’s go back to the domain of access control and see what we add for level 4:
- Control information flows between security domains on connected systems.
- Periodically review and update CUI program access permissions.
- Restrict remote network access based on organizationally defined risk factors such as time of day, location of access, physical location, network connection state, and measured properties of the current user and role.
And Level 5:
- Identify and mitigate risk associated with unidentified wireless access points connected to the network.
Have questions about CMMC Levels? LBMC can help your organization prepare for and navigate the CMMC framework. Contact us now.
